Windows updates and anti-forensics (part 1, USB devices)
Background
In this post I will be talking about feature pack updates for Windows 10 operating system and how they affect computer forensic examinations. First part covers USB forensic artifacts affected by the update.
Feature updates for Windows 10 are released by Microsoft twice a year and can be considered major updates since they include new functionality, enhancements, visualization updates and many more. Each feature update for Windows 10 has a unique version number that corresponds with month and year of planned release (for example, version 1909 had a planned release date September 2019).
From the forensic standpoint I can define three states of a system that undergoes feature update:
Pre-update – original system that had the old Windows 10.
Initial post-update – system that just underwent update with the new feature pack. After the update operating system keeps a snapshot of its original state under “C:\Windows.old\” directory. With this feature Microsoft gives users a chance to revert back to previous version of Windows 10 in case the new configuration and settings were not compatible with the applications used prior to the update. From the forensic standpoint contents of “C:\Windows.old\” would preserve all original operating system artifacts required to perform forensic examination. Referring to USB analysis those artifacts would include HKCU, HKLM\SYSTEM, HKLM\SOFTWARE, setupapi.dev.log, event logs.
Post-update – system that cleared all temporary files created during the update, and therefore fully transitioned to the new feature version. The cleanup process can either be triggered by operating system 10 days after the update, or can be manually started by user in Windows 10 storage settings. The process would apply several changes to the system, including removing “C:\Windows.old\” directory.
One way to determine the system underwent a feature update is to find a subkey under “HKLM\SYSTEM\Setup” registry key, that would have a format “Source OS (Updated on MM/DD/YYYY HH:MM:SS)”, where “MM/DD/YYYY HH:MM:SS” is the date and time of the feature update.

Assumptions and limitations
Experiments were performed on Windows 10 feature pack versions 1809 and 1903 (plus version 2004 in the bonus content at the end of this post). It is possible other feature update versions may behave slightly differently.
The experiments were focused on artifacts that could reveal time stamp information of when USB drives were plugged in to the system (first / last connected, last disconnected and historical connection events), and were not focused on other artifacts, such as for example correlation between device serial number (S/N) and volume names / labels, drive letters for mapped volumes, volume S/N and users interacted with the USB device.
Analysis of “initial post-update” (as defined in the background section of this post) was not performed, because “C:\Windows.old\” directory maintained a copy of all artifacts of the operating system prior to the update.
Summary of findings
Experiments showed Windows 10 feature update significantly impacted event logs, registries and other operating system artifacts required for forensic analysis of USB devices that were plugged in to the system prior to the update.
Initial feature pack update cleared majority of the operating system artifacts necessary to perform forensic analysis.
After the update Windows 10 created a new registry key “HKLM\SYSTEM\Setup\Upgrade\”, which will be useful for forensic examinations. Specifically, last disconnect time stamps for USB drives plugged in prior to the update can be determined based on value in “LastPresentDate” for several subkeys under: “HKLM\SYSTEM\Setup\Upgrade\Pnp\CurrentControlSet\Control\DeviceMigration\Devices\”.
Additional tests revealed if there were two feature pack updates installed, it would not be possible to determine time stamps associated with USB devices connected to the system prior to the first update. Only minimal artifacts would remain in registry that in best-case scenario would allow to determine the fact of USB device plugged in to the system at some point.
Detailed analysis
In order to demonstrate how forensic artifacts were altered by the update, I will compare “pre-update” and “post-update” states of the Windows 10 operating system, as defined in the background section of this post.
To begin with, I will show the results of forensic analysis for a system that was updated from Windows 10 version 1809 to version 1903. For the demonstration I used USB drive with device S/N 070A8314CE182019 that was attached to pre-update system on 9/3/2021 at approximately 14:49 local time / 18:49 UTC. Update to version 1903 was started on 9/3/2021 at approximately 15:33 local time / 19:33 UTC.
For each artifact described I will be providing screenshots showing before (pre-update) and after (post-update) states.
Before the update “Setupapi.dev.log” contained a record of drivers installation for USB drive S/N 070A8314CE182019. The installation started on 9/3/2021 at approximately 14:49:51 local time. After the update “Setupapi.dev.log” was re-created with the first record dated as of 9/3/2021 15:46:25 local time.
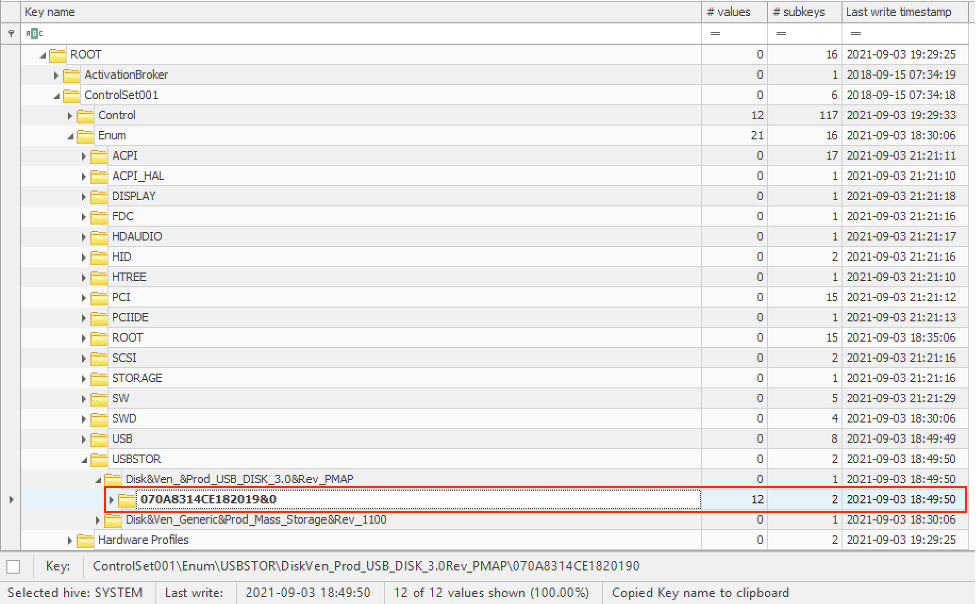
“HKLM\SYSTEM\ControlSet001\Enum\USBSTOR” registry key was removed after the update.
“HKLM\SYSTEM\ControlSet001\Enum\USB\VID_13FE&PID_5500\%S/N%” – record for USB drive S/N 070A8314CE182019 was removed after the update.
“HKLM\SYSTEM\ControlSet001\Enum\STORAGE\Volume\%S/N%” – record for USB drive S/N 070A8314CE182019 was removed after the update.
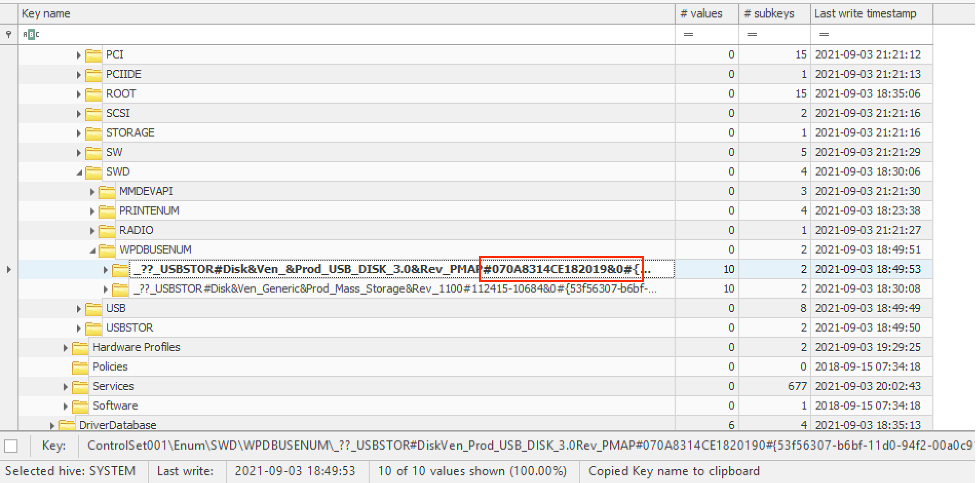
“HKLM\SYSTEM\ControlSet001\Enum\SWD\WPDBUSENUM\%S/N%” – registry key WPDBUSENUM (portable device enumerator service) containing record of USB drive S/N 070A8314CE182019 was removed after the update.
“HKLM\SYSTEM\ControlSet001\Control\DeviceClasses\{53f56307-b6bf-11d0-94f2-00a0c91efb8b}\%S/N%” – showed storage device drivers installed for USB drive S/N 070A8314CE182019. After the update this key was removed.
“System.evtx” event ID 20001 showed drivers were installed for USB drive S/N 070A8314CE182019 at approximately 14:49:54 local time. After the update event log “System.evtx” was cleared and the earliest record was at approximately 15:45:01 local time.
“Microsoft-Windows-Kernel-PnP%4Configuration.evtx” series of event IDs 400, 410, 430 referenced drivers installation for USB drive S/N 070A8314CE182019. After the update event log “Microsoft-Windows-Kernel-PnP%4Configuration.evtx” was cleared and the earliest record was at approximately 15:45:01 local time.
“Microsoft-Windows-Partition%4Diagnostic.evtx”, event ID 1006 showed a record for USB drive S/N 070A8314CE182019 at approximately 14:49:51 local time. After the update the event log “Microsoft-Windows-Partition%4Diagnostic.evtx” was cleared and the earliest record was at approximately 15:45:07 local time.
“HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\” registry key contained volume GUID {50404ddb-0ce7-11ec-b752-000c29fb8cf1} that can be cross-correlated to USB drive S/N 070A8314CE182019. After the update the volume GUID entry was removed.
Based on the experiment results, majority of the operating system artifacts containing evidence of USB devices plugged in to the system were cleared after the update. In the next section I am going to show few artifacts that did not exist before the update and could still contain some information regarding historical USB devices plugged in to the system prior to the update.
“Setupapi.upgrade.log” log file was created after the update. In my tests this log contained PnP drivers migration records for the previously initiated USB drives (including USB drive S/N 070A8314CE182019).

“HKLM\SYSTEM\Setup\Upgrade\” registry key was created after the update. The following subkeys would be of interest for USB forensics, and in our case will have records for the USB drive that was plugged in prior to the update: “Pnp\CurrentControlSet\Control\DeviceMigration\Devices\SWD\WPDBUSENUM\%S/N%”, “Pnp\CurrentControlSet\Control\DeviceMigration\Devices\USB\%S/N%”, “Pnp\CurrentControlSet\Control\DeviceMigration\Devices\USBSTOR\%S/N%”. As you can notice, “last write” time stamp was updated after the system update, and therefore cannot be relied on during forensic examinations. Value under “LastPresentDate” in the above subkeys could reveal the last time a drive was disconnected from the system.



Bonus content!
Now the question is – would any evidence of the USB drive remain if we perform another update? For these purposes on the newly updated system (version 1903) I installed additional feature update (version 2004). The “HKLM\SYSTEM\Setup\” registry key showed installation for second feature update was started on 9/6/2021 at approximately 16:41:40 local time:

Similar to previous experiments temporary installation files were cleared after the update via Windows 10 storage settings. I compared state of pre-install (version 1903) to post-install (version 2004). The experiment showed that after second update it will not be possible to determine when USB drive in question (S/N 070A8314CE182019) was plugged in. However, we would still be able to determine the fact that USB drive was plugged in at some point – based on registry key value in “HKLM\SYSTEM\MountedDevices\”

References
Windows 10 versions history (https://docs.microsoft.com/en-us/windows/release-health/release-information)
Microsoft updates terminology (https://docs.microsoft.com/en-us/troubleshoot/windows-client/deployment/standard-terminology-software-updates)
Tools used
Registry Explorer/RECmd (https://ericzimmerman.github.io/#!index.md)
USB Detective (https://usbdetective.com)






















What can be detected by the described verification algorithm after using the "USB Oblivion" cleaning utility https://www.cherubicsoft.com/en/projects/usboblivion?