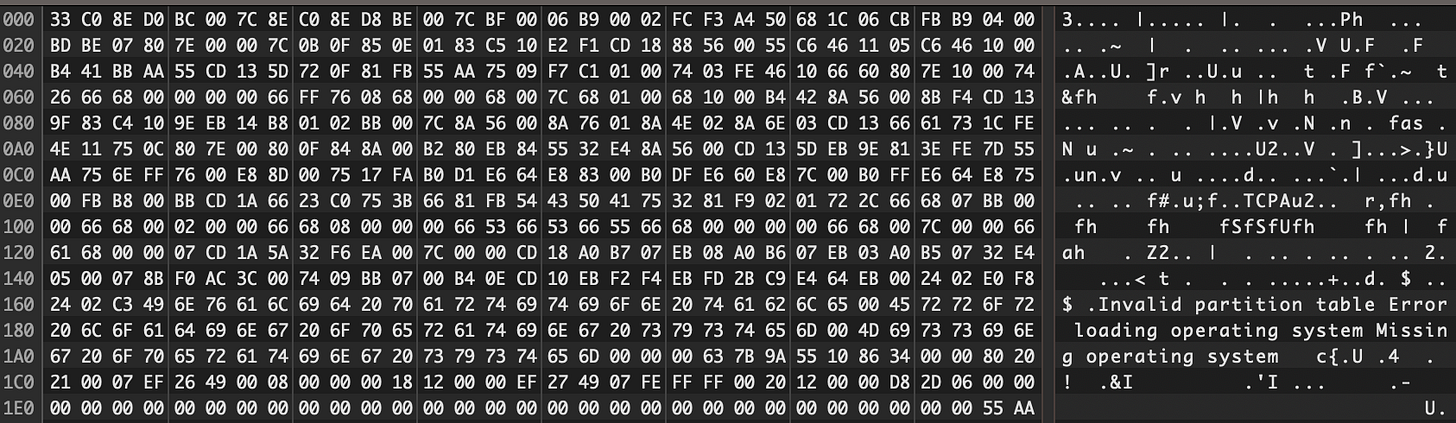
Diving into Master Boot Record
Parsing the sector 0
Partitioning scheme is a data structure that is set on a storage device during disk initialization. The scheme describes how a storage device is divided into logical sections, i.e. disk partitions. Partitioning scheme is required to be present on storage device in order for operating system to boot from that device.
Two primary partitioning schemes that are most commonly used by operating systems are Master Boot Record (MBR) and GUID Partition Table (GPT). MBR is a legacy scheme that supports up to 4 partitions per disk with a storage limit of 8TB. GPT is a modern scheme that supports up to 128 partitions, with maximum theoretical storage limitation of 9.4 ZB (9.4 billion TB).
This blog post will be specifically focusing on automated analysis of MBR, which is located at the sector 0 of a physical storage device.
MBR has a length of 512 bytes and has the following structure:
Bytes 0-445: bootstrap code
Bytes 446-461: partition table entry 1
Bytes 462-477: partition table entry 2
Bytes 478-493: partition table entry 3
Bytes 494-509: partition table entry 4
Bytes 510-511: MBR signature (0x55AA)
Each of the 4 partitions defined in MBR has a dedicated table with the length of 15 bytes:
Byte 0: Bootable flag
Bytes 1-3: Starting Cylinder-Head-Sector (CHS) address (legacy system, that specifies physical location of the partition on the disk; CHS maps to the disk's physical geometry, where the cylinder represents concentric tracks on the disk platter, the head indicates which disk surface to read from, and the sector specifies the exact segment within that track)
Bytes 4-4: Partition type
Bytes 5-7: Ending CHS address
Bytes 8-11: Starting Logical Block Addressing address (a.k.a. LBA, indicates the first logical sector of the partition)
Bytes 12-15: Size in sectors
MBR can be targeted by sophisticated malware in several ways. Malicious boot loaders and rootkits can infect the bootstrap code to maintain persistence. Destructive malware like WhisperGate, HermeticWiper can modify the MBR to prevent system boot. I wrote a tool for MBR analysis that performs the following actions:
Exports MBR
Parses partition tables
Hashes both, full MBR, and the bootstrap code section
Disassembles the bootstrap code, assuming it is written in 16-bit x86 assembly, and adds explanatory comments to clarify some basic code's functionality
The tool (link) can be used for triage and can extract MBR from either system partition or mounted disk image. See example analysis report output on the screenshot below. Try it out and let me know how it works!
References
Windows support for hard disks that are larger than 2 TB (https://learn.microsoft.com/en-us/troubleshoot/windows-server/backup-and-storage/support-for-hard-disks-exceeding-2-tb)
File System Forensic Analysis (Fourteenth Printing), by Brian Carrier (https://www.sans.org/profiles/brian-carrier/)
Tools used
X-Ways Forensics (https://www.x-ways.net/forensics/index-m.html)
MBR parser (https://github.com/ilyakobzar/dfir-tools/blob/main/mbr_parser.py)